Author:程序员犬余
PART 01 Starting with the “Good, Fast, Cheap” Dilemma
Let's begin with something you're undoubtedly familiar with.
Imagine shopping online. Your ideal scenario likely involves: high-quality goods that last long and rarely break; low prices, preferably the lowest online; and fast shipping—ideally order today, arrive tomorrow. Yet you'll find it nearly impossible to maximize all three simultaneously. Often, you get excellent quality and decent delivery, but the price isn't cheap; or you get a bargain price and acceptable delivery, but the quality is mediocre. Achieving “all three at maximum” is rare in reality.
Consider homework or exam prep: naturally, you want high scores, minimal time investment, and low stress. But reality often dictates: aiming for top marks demands significant time and effort; while opting for less effort means accepting potentially lower results.
This reflects a common “multi-objective trade-off” dilemma: we seek to satisfy multiple goals simultaneously, yet limited resources force us to prioritize.
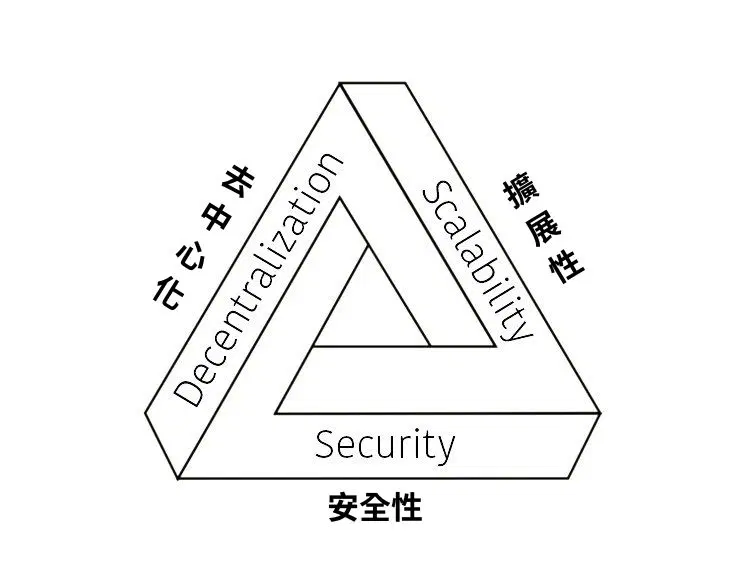
The blockchain world faces a strikingly similar conundrum, known by the somewhat intimidating term: the “Blockchain Impossible Triangle.”
Next, we'll explain this “triangle” in accessible terms.
PART 02 What Is the “Blockchain Impossible Triangle”?
The core idea behind the “Blockchain Impossible Triangle” can be summed up in one sentence: Within a blockchain system, it's extremely difficult to achieve “exceptional excellence” in all three aspects—security, decentralization, and performance—at the same time. In practice, we often have to prioritize two of them, making compromises on the third.
There are three key terms here. Let's start with the simplest explanation, then gradually add some technical details.
PART 03 Clarifying the Three Key Terms
Security: The System's Ability to Hold the Line
For ordinary users, security is most tangibly felt when:
- Your assets aren't easily stolen,
- Your transaction records can't be arbitrarily altered or erased.
From a system perspective, typical risks blockchain faces include: attempts to “erase” or rewrite completed transactions (record tampering); spending the same funds twice (double-spending attacks); or collusion among nodes to seize control of the network's accounting authority (malicious node attacks).
Major public blockchains like Bitcoin and Ethereum operate on a crucial design premise: as long as the “majority” of nodes are honest, the system remains fundamentally secure. This security boils down to one principle: successfully attacking the system would require an astronomical cost—such as controlling the vast majority of the network's computing power or staking an overwhelming amount of tokens. When this cost becomes prohibitively high, to the point where virtually no one would attempt it, the system can be deemed “sufficiently secure.”
Decentralization: Not Controlled by a Few Individuals
Decentralization can be understood through two questions. First: Who qualifies to participate in accounting and verification? Is participation limited to a few institutions? Or can anyone voluntarily join provided they meet certain hardware and network requirements? Second: Could the system be controlled by a single point? If persuading just a few nodes allows altering rules or censoring transactions, it leans toward centralization. If persuading thousands of nodes dispersed globally is required, it becomes nearly impossible “control the entire system.”
Benefits of decentralization include: censorship resistance—it's difficult for any single entity to unilaterally decide “this transaction cannot proceed”; resilience against single points of failure—even if some nodes fail or are attacked, the network as a whole remains functional; and power dispersion—no one possesses ultimate authority to “alter the ledger with a single backend command.”
Simply put: the more nodes, the greater the dispersion, and the lower the participation barrier, the more decentralized the system becomes.
Performance: How fast and affordable is it for users?
Performance in blockchain typically refers to two metrics. One is TPS (Transactions Per Second), meaning how many transactions can be processed per second. The other is latency and cost, encompassing how long a transaction takes from initiation to confirmation, and whether fees spike to unaffordable levels during network congestion.
For users, performance translates to: Do funds transfer instantly? When using decentralized applications (DApps), do they lag endlessly while charging exorbitant fees?
We can roughly define performance as: whether the system can operate quickly, stably, and cost-effectively under heavy concurrent user load.
PART 04 Why Is It Difficult to Achieve All Three at the Highest Level?
With the three concepts above, we now address the critical question: Why is it challenging in real-world engineering to achieve “exceptional security, high decentralization, and outstanding performance” simultaneously?
This difficulty primarily stems from several technical factors: the number of nodes, network propagation, and the complexity of the consensus protocol.
Decentralization vs. Performance: More Participants Slow Communication
A highly decentralized public chain typically involves numerous nodes maintaining the ledger. These nodes are distributed across different regions globally, each with varying network conditions. They must constantly communicate to exchange the latest block and transaction information.
Whenever a new transaction or block emerges, it must originate from one node, propagate through the network to others, and then be individually verified and recorded by each node before consensus is reached. More nodes and wider distribution mean: longer propagation times as messages must “travel farther” to reach most nodes; increased consensus rounds or extended waiting periods, as protocols often need to “hold off” to ensure sufficient nodes receive and validate data.
This is akin to a meeting: with three people, discussions wrap up quickly and votes are taken swiftly; with 3,000 people, even if each speaks only once, the process becomes extremely lengthy.
Therefore, when aiming for “anyone to easily run a node” and participate in validation, it implies a large number of nodes. To accommodate the network and computational capabilities of most nodes, the system cannot operate too quickly, or many nodes will fall behind. The result is this: the higher the level of decentralization, the more compromises you often have to make on performance.
Security vs. Performance: Adding an Extra Lock Slows Down the Door Opening
To enhance security, blockchain systems typically implement stricter validation rules: checking transaction validity, signature integrity, and sufficient balances; performing multiple layers of block verification to prevent malicious blocks from slipping through. Simultaneously, systems demand more “confirmations”—for instance, Bitcoin often advises “waiting for 6 block confirmations before considering a transaction secure.” This is akin to installing not just one lock, but multiple locks, ensuring the record of unlocking is nearly impossible to overturn.
These measures fundamentally trade increased computational effort and time for heightened security. Consider this analogy: A single simple lock on your door allows quick entry and exit but offers limited security. Installing multiple security doors, combination locks, and fingerprint scanners slows down daily comings and goings.
Blockchain operates similarly: Faster transaction confirmation requires fewer verification steps and shorter wait times, but this reduces the system's “security margin” against attacks. Therefore, when you tighten security, performance is often sacrificed to some extent.
Security vs. Decentralization: Centralizing Power vs. Distributing Authority
Intuitively, concentrating critical accounting and verification authority in a few powerful nodes allows equipping them with robust hardware and protection systems. Troubleshooting and maintenance also become more efficient. This is common in traditional centralized systems, such as bank data centers or payment company servers, where unified management simplifies security policy deployment.
However, in a blockchain system pursuing decentralization, if the vast majority of ordinary users struggle to run a full node and only a few institutions control key accounting rights, the degree of decentralization significantly diminishes from a “power dispersion” perspective.
Conversely, if the goal is to enable diverse participants from various backgrounds and regions to easily run nodes without relying on a handful of “super nodes,” the protocol design must account for the fact that most nodes have average hardware and network capabilities. It cannot demand that every node perform exceptionally complex and resource-intensive computations, as this would eliminate ordinary nodes, leaving only a small group of powerful nodes to sustain the network.
Thus: Extreme emphasis on security can be achieved through “a few supernodes + robust protection,” but this leads to greater centralization. Emphasizing broad participation and power dispersion requires accepting that individual nodes are less powerful, relying more on the protocol's overall design to ensure security. This is the tension between security and decentralization.
PART 05 Bitcoin, Ethereum, Solana: Where Do They Stand in the Triangle?
Having covered the principles, let's examine three concrete examples: Bitcoin, Ethereum, and Solana. Each is highly representative yet has made distinct choices within the “impossible triangle.”
Bitcoin: Security + Decentralization Priority, Accepting “Relative Slowness”
Bitcoin was originally conceived to provide a globally accessible peer-to-peer electronic cash system independent of any single institution. Consequently, its design emphasizes two key aspects: security, achieved through Proof-of-Work (POW) combined with a massive computational network to resist attacks; and decentralization, enabling anyone to run a node and validate transactions and blocks across the entire network.
The Bitcoin network exhibits several distinct characteristics: a large number of nodes distributed globally, making it difficult for any single entity to control; block generation occurs within minutes, requiring multiple blocks to confirm a transaction; and relatively low TPS, making it better suited as an underlying network for “store of value” and “large-value settlements.”
From the perspective of the Impossible Trinity, Bitcoin prioritizes the “security + decentralization” corner, adopting a relatively conservative approach to performance. It prioritizes stability over speed.
Ethereum: Striking a Balance Among the Three, with Scaling Solutions to Boost Performance
Building upon Bitcoin, Ethereum introduced enhanced smart contract capabilities, transforming the blockchain into a programmable platform. This necessitates balancing security and decentralization while addressing performance pressures from extensive applications.
Ethereum's core approach is: The main chain (L1) continues emphasizing security and decentralization. Initially using POW, it later switched to POS, but the core goal remains ensuring consensus security, positioning the main chain as the “final settlement layer”—akin to a “supreme court” role. When facing performance bottlenecks, rather than making radical changes to the main chain, scaling solutions like Layer 2 and Rollups are employed. These offload massive transaction volumes to secondary layers or sidechains for processing, then “bundle” the results back to the main chain for final confirmation. The main chain solely handles final settlement.
This approach yields a mainchain with modest TPS but maintains high security and decentralization standards. The multi-layered ecosystem mitigates performance issues to a significant degree. Within the Impossible Trinity framework, Ethereum seeks equilibrium at the triangle's center—prioritizing “security + decentralization” on the mainchain while enhancing performance through peripheral layers.
Solana: Prioritizing Performance While Accepting Some Centralization
Solana's design goal is straightforward: a high-performance public chain. It aims for extremely high TPS and ultra-low latency to support high-frequency trading and complex applications.
To achieve this, Solana imposes higher demands on node hardware and network bandwidth in its technical approach and engineering implementation. It employs more aggressive consensus and data processing solutions to minimize latency at every stage.
The outcome is that Solana's theoretical and actual TPS significantly outperform traditional public chains. However, the number of participants capable of running full nodes is substantially lower than Bitcoin or Ethereum, often sparking debates about its decentralization and censorship resistance.
Thus, within the Impossible Trinity, Solana leans toward the “Performance + Security” combination, making certain compromises in decentralization.
A mental “triangular coordinate system”
If you plot “security,” “decentralization,” and “performance” as a triangle, you might visualize it like this: Bitcoin sits near the “security + decentralization” corner, Solana leans toward the ‘performance’ corner, while Ethereum occupies the center, slightly tilted toward “security + decentralization.” This isn't a precise mathematical diagram but a mental map to help you quickly grasp the positioning of different public blockchains.
PART 06 Why Should Ordinary Users Care About the “Impossible Triangle”?
Many encountering the “blockchain impossible triangle” for the first time assume it's solely for technical personnel. In reality, it holds equal value for everyday users.
Shifting Focus from “Speed” to “The Cost of Speed”
When you see a new public chain or project touting its high TPS, low fees, or fast confirmations, ask yourself: What was sacrificed to achieve this? Was security compromised? Was decentralization reduced?
Understanding the Impossible Triangle helps you maintain rationality toward claims of “ultra-secure, fully decentralized, ultra-high-performance, and virtually cost-free” solutions. Recognize that achieving all three without trade-offs is nearly impossible in engineering. “having it all without any trade-offs.”
Viewing Public Chain Debates More Objectively
Within communities, you often see one camp emphasizing their public chain's high TPS, while another highlights greater decentralization and security, with both sides questioning the other's “obsolescence” or “inadequacy.”
If you grasp the Impossible Triangle, it becomes clearer that many debates are actually arguments over different trade-off solutions rather than one side being absolutely correct. The application scenarios for different public chains are inherently not identical. From another perspective, no single trade-off is “perfect”; it's only about whether it suits a particular scenario.
Laying the Groundwork for Understanding More Concepts
In the blockchain space, many subsequent technologies and terms—such as Layer 2, Rollups, sidechains, sharding, modular blockchains, and various new consensus algorithms and architectural designs, are essentially attempts to rearrange the weights within the triangle: Which layer prioritizes security? Which layer emphasizes performance? How is decentralization distributed across the overall architecture?
If you first grasp the fundamental logic of the “impossible triangle,” understanding these concepts becomes much easier.
PART 07 Can the Impossible Triangle Be “Broken” in the Future?
Finally, let's address a question on many minds: Could a technology emerge that maximizes security, decentralization, and performance simultaneously?
From an engineering perspective, a more accurate statement is: A completely cost-free “ultimate solution” is unlikely, but continuous innovation can collectively elevate all three aspects within the same resource constraints.
Engineering “Partial Breakthroughs”
Over time, progress occurs across multiple fronts: consensus algorithms become more efficient, network protocols are optimized for faster and more stable propagation, and hardware performance advances, enabling nodes to process greater volumes of data.
These advancements produce a synergistic effect: without altering the fundamental trade-offs, they blunt the sharp edges of the “triangle.” In other words, where the three pillars might previously have reached only 6 points, they can now achieve 7 or 8 points at the same cost. While trade-offs remain necessary, their cost-effectiveness continually improves.
Multi-Layer Architecture: Addressing Different Needs at Different Layers
Another crucial direction involves reorganizing this triangle through layering and modularization:
- The main chain (L1) prioritizes security and decentralization, serving as the final settlement and record layer; while Layer 2, application chains, and other layers prioritize performance and user experience. The entire system collaborates across layers to deliver a superior overall experience.
This mirrors the real-world financial system: central banks and clearing systems handle final settlement and stability, while commercial banks and payment institutions manage user experience and high-frequency transactions. Blockchain's multi-layer architecture is attempting a similar approach.
A Realistic and Optimistic Conclusion
Therefore, a more realistic answer is: the Impossible Trinity won't be “eliminated,” but it can be “mitigated.” We cannot expect a perfect solution without any trade-offs, but we can anticipate that as technology evolves, users will gradually gain “more cost-effective combinations”: security remains assured, decentralization is sufficient to resist abuse, and performance is adequate to support more practical applications.
PART 08 The “Choose Two Out of Three” Dilemma in Daily Life
Recall the scenario at the beginning of this article: When shopping online, you're unlikely to consistently find products that are “highest quality + lowest price + fastest delivery.” Similarly, when preparing for exams, it's rare to achieve “highest scores + minimal time investment + zero effort.”
Most of the time, we must prioritize based on our needs: sometimes valuing quality over cost, accepting a higher price; other times prioritizing speed, accepting extra effort in preparation.
Blockchain system design follows the same principle: some emphasize security and decentralization, accepting performance trade-offs; others pursue extreme performance, accepting pressure on decentralization and security boundaries; still others seek a “sufficiently balanced” middle ground.
Understanding the “Blockchain Impossible Triangle” isn't about memorizing a technical term. It's about asking yourself this question when evaluating public chains and projects: What trade-offs did it make between security, decentralization, and performance? Does this choice suit the problems it aims to solve? Does it suit me?
When you habitually think this way, you're already closer to grasping the real operational logic of the blockchain world than most users who only look at marketing slogans.