Author:Ha ha ha ha
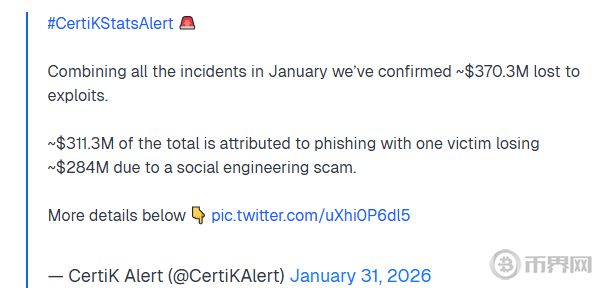
According to a report released by blockchain security firm CertiK, in January 2026, the amount of cryptocurrency stolen due to hacking and fraud surged to $370.3 million, nearly four times that of the same period last year, setting a record for the highest monthly loss in nearly a year. Among these, a single phishing attack targeting hardware wallets resulted in a staggering $284 million loss.
According to a report released by blockchain security firm CertiK, cryptocurrency thefts caused by hacking and fraud surged to $370.3 million this month, nearly four times the amount stolen in the same period last year, setting a record for the highest monthly loss in nearly a year. As attack methods become increasingly sophisticated, shifting from technical vulnerabilities to exploiting human weaknesses, we can't help but ask: Are our crypto assets still safe?
We will analyze the cryptocurrency theft incident in January 2026 and discuss with you how to protect your digital currency assets.
January Cryptocurrency Theft Surges
The first month of 2026 became the "darkest hour" for cryptocurrency security, with losses exceeding $370 million in a single month. Let's look at these alarming figures:
According to CertiK's "January 2026 Cryptocurrency Security Report," total losses from security incidents that month reached $370.3 million, a new high in nearly 11 months, representing a staggering 278% increase compared to January 2025. PeckShield's statistics also show that there were 16 protocol hacking incidents alone, resulting in losses of $86.01 million, a 13.25% increase from the previous month. These data clearly demonstrate that security threats are rapidly escalating.
CertiK Security Alert
The most shocking incident was a massive phishing attack targeting Trezor hardware wallet users. Attackers impersonated official customer service, tricking users into entering mnemonic phrases on a highly realistic fake website, resulting in one user losing 1,459 Bitcoins and 20,500 Litecoins, a total value of approximately $284 million.
Observations reveal a correlation between the nearly fourfold surge in cryptocurrency thefts in January and market volatility. This reminds us that security efforts and vigilance cannot be relaxed during periods of market downturn, especially in defense against new social engineering attacks.
Tracing the Roots: A Double Blow of Vulnerabilities and Fraud
The nearly fourfold surge in cryptocurrency thefts in January reveals a double blow of "refined technical vulnerabilities" and "humanized fraud methods." Attackers utilize both technical expertise and exploit human weaknesses.
Technical Vulnerabilities
We found that technical vulnerabilities in smart contracts and DeFi protocols remain frequently exploited entry points for hackers. These attacks are often direct and brutal, resulting in significant losses once successful.
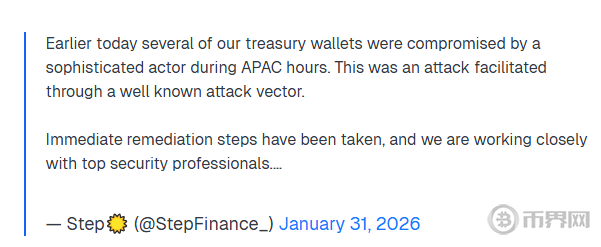
For example, in January 2026, Step Finance, a DeFi protocol based on the Solana blockchain, was attacked, resulting in the theft of approximately $28.9 million in assets and the breach of multiple protocol vaults. Around the same time, Truebit Protocol lost 8,535.36 ETH (approximately $26.44 million at the time) due to a serious integer overflow vulnerability in its token purchase price calculation logic.
CertiK Security Alert
These events reveal a harsh reality: the root cause of such vulnerabilities often lies in insufficient code auditing before project launch or inadequate economic model design. Even in programs running on the blockchain, minor flaws in their underlying logic can be amplified, causing huge sums of money stored within to vanish instantly.
This reminds us that behind the principle of "code is law" lies an extremely rigorous requirement for code quality.
Escalating Fraud
The biggest case in January—a massive phishing attack targeting Trezor hardware wallet users—is a typical example of social engineering attacks.
Attackers impersonated official customer service representatives, using carefully crafted scripts to trick users into entering mnemonic phrases on highly realistic fake websites. This resulted in one user losing 1459 Bitcoins and 2.05 million Litecoins, a total value of $284 million. Another common tactic is wallet pumping (such as the Monkey Drainer scam), which doesn't steal private keys but tricks users into signing malicious authorizations, allowing attackers to transfer specific tokens. This has caused losses exceeding $4.3 million in hundreds of wallets.
In short, the biggest threat is shifting from "code vulnerabilities" to "human vulnerabilities." Even the most robust technical fortresses are vulnerable to being breached from within by "psychological engineering." Raising security awareness is no longer an option, but a necessity.
How to Build a Crypto Asset Security Defense Line?
CoinMeta reminds you: Faced with the severe security situation of a nearly fourfold increase in cryptocurrency theft in January, building a multi-layered, comprehensive defense system is the only way to protect digital assets.
Personal Protection: Security Habits Above All Else
We recommend that every user adhere to the following ironclad rules:
**Never Disclose:** Genuine official personnel will never ask for your mnemonic phrase or private key. Anyone making this request is a scammer.
**Official Verification:** Always verify all software updates, airdrop information, and customer service communications through the project's official website or announcement channels. Be wary of links circulating on social media.

Distributed Storage Strategy
Adopt a strategy of using hot wallets for small transactions and cold wallets for large savings. Use hardware wallets such as Ledger or Trezor to store core assets, avoiding keeping all assets in one place.
**Industry Evolution: From Emergency Response to Immunity:** Security is not only the user's responsibility but also requires the industry as a whole to build a defense-in-depth system. In the $284 million theft in January, security company ZeroShadow successfully froze approximately $700,000 of stolen funds through real-time on-chain monitoring, preventing its complete "laundering." This demonstrates the effectiveness of professional emergency response mechanisms.
In the long run, the industry needs to promote stricter smart contract code auditing standards and establish a platform-level threat intelligence sharing network across exchanges and protocols. For example, 60% of mainstream projects have increased their security budgets to 12-15% and shifted to a security service subscription model for continuous protection, which is far more effective than a single audit.
Conclusion
The increase in cryptocurrency theft in January 2026 is an inevitable result of the combination of technical vulnerabilities and advanced fraud methods. It clearly reveals that the battlefield for digital asset security has expanded from the single code layer to the complex psychological layer of human nature. Protecting asset security is no longer just the responsibility of developers or security companies, but a mandatory course for every holder.
CoinMeta believes that building a more secure crypto ecosystem requires the industry to continuously deepen its efforts in smart contract auditing and threat intelligence sharing, and also depends on whether each user can build a strong psychological defense of "never revealing their mnemonic phrase." Only when technology and awareness advance in tandem can digital wealth truly enjoy reliable security.
The above content is about "Cryptocurrency Theft Surges Nearly Fourfold in January: Are Crypto Assets Still Safe?" For more information on cryptocurrency security, please visit CoinWorld.com.
Disclaimer: Readers are advised to strictly abide by local laws and regulations. This article is for reference only and does not constitute any investment advice.










